Nowadays, the development of web applications is going more and more and attackers also continue to learn many new techniques to compromise the security of web application. So, Web application security becomes more essential as web application continues to grow.
Here is a list of top most common web application attacks
- SQL Injection
In SQL injection also known as SQLI, an attacker destroys any SQL database by inserting the malicious code in SQL statements to access information. Attackers can edit or access databasess by altering SQL commands and can also delete the entire database of any user through SQL injection.
For Example:
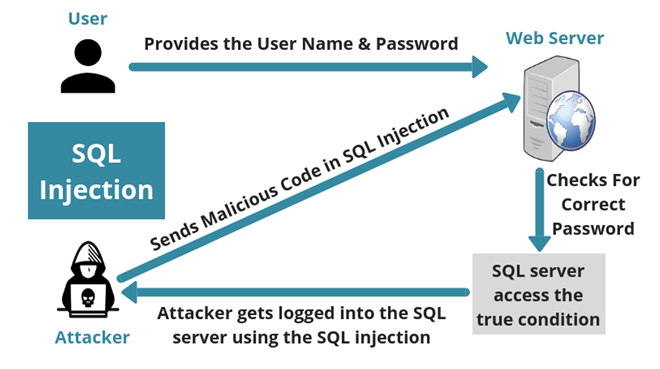
- Cross-Site Scripting (XSS)
In a cross-site scripting attack, an attacker injects malicious scripts in a web application which allows an attacker to steal each visitor’s session cookies.
XSS attack can be difficult to find or remove from a web application. The only way is to identify this type of flaw is to perform a security review of the code and search for all places where input from an HTTP request could possibly make its way into the HTML output.
For Example:

- Cross-Site Request Forgery (CSRF)
CSRF also is known as XSRF, or Session Riding is a type of attack which forces a user to run unwanted actions in a web application. Unlike cross-site scripting (XSS), which exploits the trust a user, has for a particular website, CSRF exploits the trust that a website has in a user’s browser.
For Example:

- Sensitive Data Exposure
Sensitive data exposure occurs when a web application fails to protect sensitive data from being revealed to illegitimate users. Sensitive data can be account number, credit card number, banking password, personal information that can cause financial loss, hijacking of identification.
Exposure of sensitive data can be protected by disabling auto-completion on forms that collect data, Disable caching on forms, using the latest encryption algorithms and by using the standard security technology like SSL or TSL which ensures data is private.
For Example:

- Remote Code Execution
In this type of attack, an attacker exploits a vulnerability of a system which allows the attacker to run commands on the targeted system. Attackers using code execution vulnerabilities may perform any action that they desire on the targeted system no matter where the system is geographically located.
For Example:

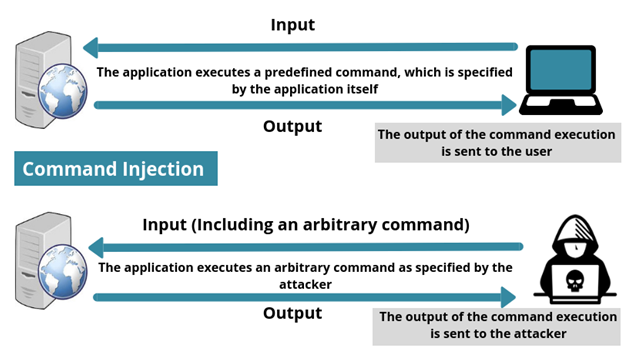
- Command Injection
In a command injection attack, an attacker executes arbitrary commands on the host operating system via a vulnerable application. In a command injection attack, an attacker can control one or multiple commands that are being executed on a system.
It occurs when an attacker attempts to execute system level commands through a vulnerable application.
For Example:
- Remote File Inclusion (RFI)
In remote file inclusion attack, an attacker exploits the vulnerability of a web application by including a remote file in a web application that dynamically executes scripts or runs on an external file in the real-time. The main objective of an attacker is to upload malware in a web application from a remote URL.
The consequences of a successful RFI attack include Remote Code Execution (RCE), where an attacker gets complete control of the exploited web application and can access the private information.
For Example:

- Local File Inclusion (LFI)
Local File Inclusion is similar to Remote File Inclusion vulnerability except instead of including remote files, only local files i.e. files on the current server can be included for execution.
In Local File Inclusion attack, an attacker tricks the web application in including files on the web server by exploiting functionality that dynamically includes local files or scripts.
For Example:

- Buffer Overflow
When more than enough data gets placed by the program, the extra data overflow which causes data leakage into other buffers and corrupts data that they were holding. There are two types of buffer overflows-: stack-based and heap-based.
In a buffer-overflow attack, the extra data sometimes holds some instructions for actions intended by the attacker; for example, the data could trigger a response that damages files, modify data or discloses private information.
For example:

- Cookie Poisoning
In cookie poisoning, an attacker modifies the content of a cookie (personal information which is stored in a user’s computer) to get the unauthorized information about the user/client for purposes such as identity fraud.
Cross-Site Scripting, Buffer Overflow, and SQL Injection attacks can be achieved through cookie poisoning.
For example:

How to stay protected against web application attacks
Here are some suggestions your business can follow to stay protected against these types of web application attacks:
Vulnerability scanner
Today, we can see a number of vulnerabilities that are lurking at the client-side as well as server-side. By exploiting these vulnerabilities, the attackers can launch various types of web application attacks and can make a web resource unavailable to its users. A vulnerability scanner discovers vulnerabilities and gives a unique perspective on where the vulnerabilities are, how dangerous they are and how to mitigate them.
Web application firewall
Web application firewall protects applications from a wide range of web application attacks such as SQL injection, zero-day exploits; session hijacking and many more which traditional network firewalls may not be capable of doing.

Haltdos WAF solution uses machine learning to automatically and accurately identify legitimate traffic from malicious traffic using its patent-pending technology. It also has in-built SSL offloading and load balancing capabilities.




