The cybersecurity landscape has fundamentally transformed. Modern cyberattacks are no longer crafted by human hackers alone—they’re orchestrated by artificial intelligence systems that learn, adapt, and strike with unprecedented speed and sophistication.
As we navigate through 2025, enterprises face a critical inflection point. Threat actors have weaponized AI to create attacks that evolve faster than traditional security measures can respond. For organizations in India—now Asia’s second-most targeted nation for cyber threats—the urgency to modernize defenses has never been greater.
This article explores why AI-driven attacks are outpacing conventional security solutions and how Indian enterprises can leverage intelligent, indigenous cybersecurity platforms to protect their digital assets.
The Democratization of Cybercrime Through AI
Artificial intelligence has fundamentally altered the economics of cybercrime. What once required specialized technical expertise, extensive coding knowledge, and significant time investment can now be accomplished in minutes with AI-powered tools.
Modern threat actors leverage AI to automate previously complex tasks: generating sophisticated malware, crafting contextually perfect phishing messages, creating synthetic identities with realistic voice patterns, conducting automated vulnerability assessments, circumventing security challenges, and orchestrating large-scale coordinated bot attacks.
This technological shift has transformed the threat landscape. Entry-level attackers can now execute enterprise-level breaches. The barrier to cybercrime has collapsed, resulting in a dramatic surge in attack frequency and sophistication. Indian financial institutions, fintech platforms, and e-commerce websites face relentless automated assaults daily, with phishing incidents alone experiencing a threefold increase in recent years.
The traditional model of cybersecurity—where defenders maintained a technological edge—has been disrupted. Attackers have seized the initiative, and organizations must fundamentally rethink their defensive strategies.
Adaptive Threats: When Attacks Learn Faster Than Defenses
The true danger of AI-powered cyber attacks extends beyond mere automation. These systems possess the ability to learn, adapt, and evolve in real-time, creating a dynamic threat environment that static defenses cannot address.
Malicious AI systems analyze defensive responses and modify attack vectors accordingly. They rotate infrastructure elements instantly, alter behavioral signatures to evade detection systems, and generate novel attack payloads dynamically based on what succeeds and what fails.
Consider the implications: intelligent botnets that adjust strategies based on defender responses, phishing systems that refine their approach with each interaction, and malware that autonomously rewrites its code to bypass detection mechanisms.
These scenarios are not theoretical future threats—they represent the current state of cyber warfare.
Legacy security architectures—signature-based antivirus solutions, static rule-based web application firewalls, and manual monitoring systems—were engineered for a different era. They cannot match the pace of machine-speed adaptation and evolution.
The Innovation Gap: Why Attackers Move Faster
A harsh reality defines modern cybersecurity: cybercriminals consistently adopt emerging technologies faster than legitimate enterprises.
The reasons are structural. Threat actors operate without compliance requirements, procurement bureaucracy, or approval hierarchies. They experiment rapidly, deploy innovations immediately, and face no consequences for failed experiments. Speed is their competitive advantage.
Enterprises, conversely, navigate complex organizational dynamics. Security modernization requires budget justification, stakeholder alignment, lengthy procurement cycles, and integration with legacy systems. Many organizations lack teams trained in AI-driven security operations, and risk aversion often delays adoption of cutting-edge defensive technologies.
This asymmetry creates a perpetual disadvantage. While attackers innovate, defenders react. To reverse this dynamic, organizations must embrace proactive, AI-enabled security architectures that match the speed and sophistication of modern threats.
The Bot Explosion: When Half the Internet Isn't Human
Today’s internet traffic presents a startling reality: between 50-60% of all web traffic originates from automated bots rather than human users. More concerning, AI has enabled these bots to mimic human behavior with such fidelity that even advanced detection systems struggle to differentiate legitimate users from malicious automation.
These sophisticated bots execute a wide range of attacks: credential stuffing operations that test stolen username-password combinations, large-scale data scraping to harvest sensitive information, competitive price intelligence gathering, payment card validation attacks, automated fake account creation, distributed denial-of-service campaigns, and systematic API exploitation.
Indian digital platforms—particularly e-commerce sites, banking systems, and event ticketing services—experience massive automated attack waves, especially during high-traffic periods like festive seasons and major cultural events.
Without AI-powered bot mitigation, organizations face severe consequences: direct revenue loss from fraud and service disruption, escalating fraudulent transactions, infrastructure strain from malicious traffic, and erosion of customer trust as user experience degrades.
This threat landscape demands sophisticated bot protection that can distinguish legitimate automation from malicious activity in real-time—a capability that defines next-generation security platforms.
Emerging AI-Driven Attack Vectors
The convergence of AI and cybercrime has spawned entirely new categories of threats that traditional security frameworks never anticipated.
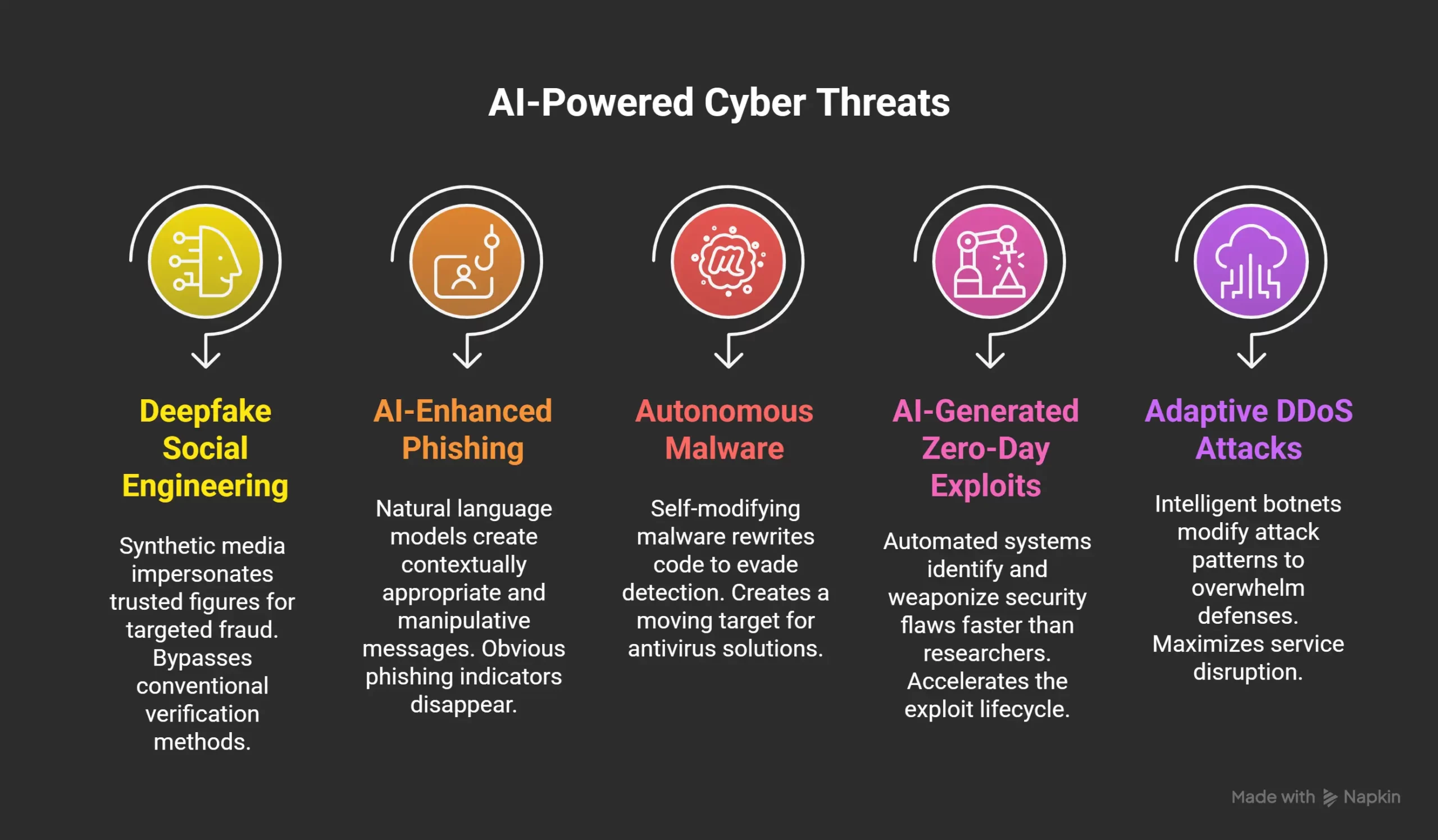
- Deepfake Social Engineering: Attackers now deploy synthetic media to impersonate executives, government officials, or business partners with startling authenticity. Voice and video deepfakes enable highly targeted fraud that bypasses conventional verification methods.
- AI-Enhanced Phishing: Modern phishing campaigns leverage natural language models to create perfectly crafted messages—contextually appropriate, grammatically flawless, and psychologically manipulative. The obvious indicators that once helped users identify phishing attempts have disappeared.
- Autonomous Malware: Self-modifying malware rewrites its code dynamically to evade signature-based detection, essentially creating a moving target that traditional antivirus solutions cannot track.
- AI-Generated Zero-Day Exploits: Automated vulnerability discovery systems can identify and weaponize security flaws far faster than human security researchers, dramatically accelerating the exploit lifecycle.
- Adaptive DDoS Attacks: Intelligent botnets continuously modify attack patterns, traffic characteristics, and targeting strategies to overwhelm defensive systems and maximize service disruption.
These attack vectors represent a fundamental shift in the threat landscape. Outdated security tools fail not due to poor implementation but because the underlying threat model has been revolutionized.
The Defense Innovation Imperative
Despite these accelerating threats, many organizations continue to rely on security architectures designed for a bygone era.
Common defensive approaches include static web application firewall rules that cannot adapt to novel attacks, signature-based detection systems that require known threat patterns, manual security monitoring that operates at human speed, reactive incident response that addresses breaches after they occur, and legacy antivirus solutions that miss polymorphic threats.
These approaches share a critical limitation: they were engineered for human-speed, predictable attacks. They cannot defend against machine-speed, adaptive threats.
To effectively counter AI-driven attacks, organizations must deploy AI-driven defenses. This principle guides the development of next-generation security platforms.
Indigenous AI Defense: The Haltdos Advantage
As a proudly indigenous cybersecurity platform, Haltdos has engineered comprehensive solutions specifically architected for modern, AI-powered threat environments. Our Made-in-India technology stack delivers enterprise-grade protection aligned with the unique challenges facing Indian organizations.
- Advanced Web Application and API Protection (WAAP): Haltdos employs AI and machine learning algorithms to detect anomalous behavior patterns that indicate attacks. Our system provides protection against zero-day exploits through behavioral analysis rather than signature matching, analyzes each request contextually to identify malicious intent, and continuously updates protection rules without manual intervention.
- Intelligent Bot Protection: Our bot mitigation technology distinguishes beneficial automation from malicious bots, identifies sophisticated bots that mimic human behavioral patterns, and stops scraping attempts, brute force attacks, and fraud operations in real-time before they impact services.
- Multi-Layer Anti-DDoS Defense: Haltdos identifies attack patterns characteristic of AI-driven botnets, implements mitigation across network, transport, and application layers, and responds to threats at millisecond scale to maintain service availability during attacks.
- Comprehensive API Security: Our API protection detects automated abuse patterns targeting your application interfaces, prevents bot-driven credential stuffing and account takeover attempts, and secures both documented APIs and shadow endpoints that pose hidden vulnerabilities.
- DNS Security Layer: Haltdos DNS firewall blocks malware communication channels at the DNS level, prevents botnet command-and-control connections, and adds an additional security layer before threats reach your network perimeter.
AI-powered threats demand AI-powered defenses. Haltdos delivers precisely this capability—innovative technology developed in India, deployed globally.
Reimagining Security: Automation Versus Automation
The future of cybersecurity lies in autonomous protection systems that match the speed and adaptability of automated attacks.
Cyber threats will continue to evolve along predictable trajectories: increasing velocity, enhanced sophistication, unlimited scalability, and growing unpredictability.
Only AI-driven, real-time, automated defense architectures can effectively counter these characteristics.
Manual security operations—however skilled—cannot process millions of bot requests per second, respond to real-time malware mutations, or adapt instantly to shifting attack patterns.
The path forward requires embracing artificial intelligence as the foundation of enterprise security strategy.
The AI-driven cyber war is not approaching—it has arrived. Organizations that continue relying on legacy defensive frameworks will face increasing breaches, not due to negligence but because the threat environment has fundamentally evolved beyond their security architecture’s capabilities.
Modern enterprise security requires AI-powered threat detection, automated response systems, and defensive automation at every layer of your infrastructure.
Haltdos—India’s most advanced indigenous cybersecurity platform—leads this transformation, delivering comprehensive protection engineered for the AI era.
The question facing every organization is not whether AI-powered attacks will target your systems. They already are.
The critical question is whether your defenses are intelligent enough, fast enough, and adaptive enough to protect your business in this new reality.
Protect Your Enterprise with Next-Generation Security
Discover how Haltdos’ AI-powered, Made-in-India cybersecurity solutions can defend your organization against evolving threats. Schedule a personalized demonstration today and experience the future of enterprise security.




