API security is no longer a mere industry catchphrase; it has become an indispensable pillar of contemporary digital infrastructures. As we advance into 2025, the realm of API threats is increasingly intricate and sophisticated.
Organizations must not only stay informed but also proactively fortify their defenses against evolving attack vectors and emerging technologies to strengthen their overall API security stance.
Here are the pivotal API security predictions for 2025 that every enterprise should carefully consider:
The Surge of AI-Driven API Offensives and Defensive Strategies in 2025
While 2023 witnessed an uptick in API-specific attacks, by 2025, this pattern has significantly intensified, with AI-powered assaults emerging as a dominant menace. Malicious actors are now harnessing artificial intelligence and machine learning to:
- Expedited Reconnaissance: Swiftly pinpoint and map API endpoints, decipher their operational logic, and uncover inherent vulnerabilities.
- Crafting Evasive Payloads: Engineer highly advanced and adaptable attack payloads capable of circumventing conventional security safeguards.
- Orchestrating Sophisticated Bots: Deploy more intelligent, human-like bot attacks that mimic legitimate user behavior to exploit APIs.
- Exploiting Business Logic: Concentrate on flaws within an API’s inherent business logic, leading to fraudulent activities, data manipulation, or service disruption rather than mere data exfiltration.
The Defensive Countermeasures: Leveraging AI for Superior API Protection
To counteract these sophisticated threats, the reliance on AI and machine learning for API security has become indispensable. Enterprises are now widely adopting AI-powered solutions to:
- Real-time Threat Detection: Analyze vast volumes of API traffic to identify and block malicious requests, even those exhibiting novel patterns.
- Behavioral Anomaly Identification: Precisely detect deviations from typical API usage, signaling compromised accounts, insider threats, or advanced attack methodologies.
- Automated Incident Response: Prioritize and automate responses to security incidents, thereby minimizing human intervention time and accelerating damage mitigation.
- Proactive Security Analytics: Anticipate potential future threats by scrutinizing historical data and recognizing emerging attack trends.
While AI systems offer formidable capabilities, it’s crucial to remember that they augment, rather than replace, human expertise.
Proficient security professionals remain essential for the configuration, oversight, and fine-tuning of these cutting-edge systems.
Shifting Security Left: Integrating API Security into DevSecOps Core
The imperative to embed API security directly into the software development lifecycle has considerably matured by 2025.
It is no longer an afterthought but an integral component of the DevSecOps pipeline. This “shift left” methodology aims to pinpoint and rectify vulnerabilities early, drastically lowering both costs and associated risks.
Key practices include:
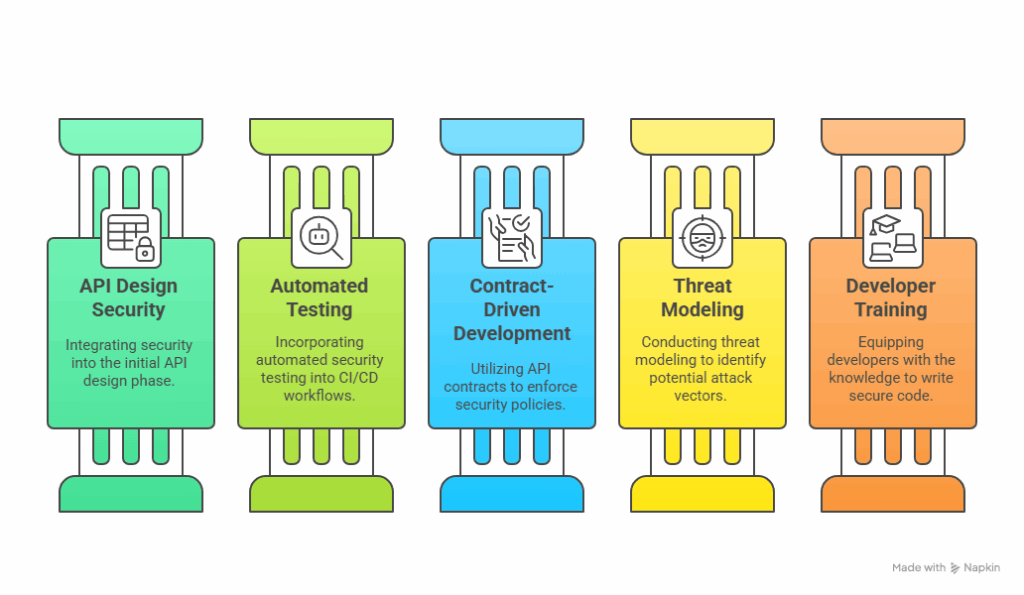
- API Design-First Security: Security considerations are intrinsically woven into the initial API design phase, stipulating authentication, authorization, data validation, and rate limiting from inception.
- Automated Security Testing in CI/CD: Incorporating automated DAST (Dynamic Application Security Testing) and SAST (Static Application Security Testing) tools into Continuous Integration/Continuous Delivery workflows to scan APIs for vulnerabilities with each code commit.
- Contract-Driven Development with Security: Utilizing OpenAPI/Swagger specifications to delineate API contracts, then enforcing security policies and validating against these established agreements.
- Standardized Threat Modeling: Consistently conducting threat modeling for all new and updated APIs to identify potential attack vectors and engineer robust defensive measures.
- Developer-Empowered Security Training: Equipping developers with the requisite knowledge and tools to write secure API code, comprehend common vulnerabilities, and adopt secure coding practices.
By fostering a shared security responsibility throughout the development continuum, organizations can construct inherently more resilient and dependable API infrastructures.
The Evolution and Widespread Adoption of API Security Standards & Frameworks
In 2025, the once-fragmented landscape of API security is giving way to more widely accepted and refined standards.
These established guidelines offer a vital blueprint for organizations aiming to build and sustain secure API ecosystems.
Anticipate heightened adherence to:
- OpenAPI Security Best Practices: Beyond mere documentation, organizations are leveraging OpenAPI specifications to programmatically enforce security requirements.
- OWASP API Security Top 10 (Updated): This continually evolving compilation remains a foundational reference, with newer vulnerabilities such as BOLA (Broken Object Level Authorization) and business logic flaws gaining prominence.
- Industry-Specific Regulations & Compliance: Stricter enforcement of data privacy regulations (like GDPR, CCPA, and emerging regional equivalents) directly influences API design, data handling protocols, and consent mechanisms.
- Zero Trust Architecture for APIs: Implementing Zero Trust principles where every API request undergoes rigorous authentication, authorization, and continuous validation, irrespective of its origin.
- API Governance Frameworks: Formalizing policies and procedures for overseeing the entire API lifecycle—from design and development to deployment, monitoring, and eventual deprecation—all with a resolute focus on security.
Staying abreast of the latest revisions to these standards is not just a recommended practice; it represents a crucial imperative for maintaining a robust security posture and averting costly breaches.
The Emergence of Specialized Cloud-Native API Security Solutions
As microservices and cloud-native architectures increasingly dominate enterprise IT, conventional web application firewalls (WAFs) frequently prove inadequate for safeguarding intricate API environments.
2025 is witnessing a significant proliferation of specialized, cloud-native API Security Solution meticulously crafted for this contemporary paradigm.
These cutting-edge solutions provide:
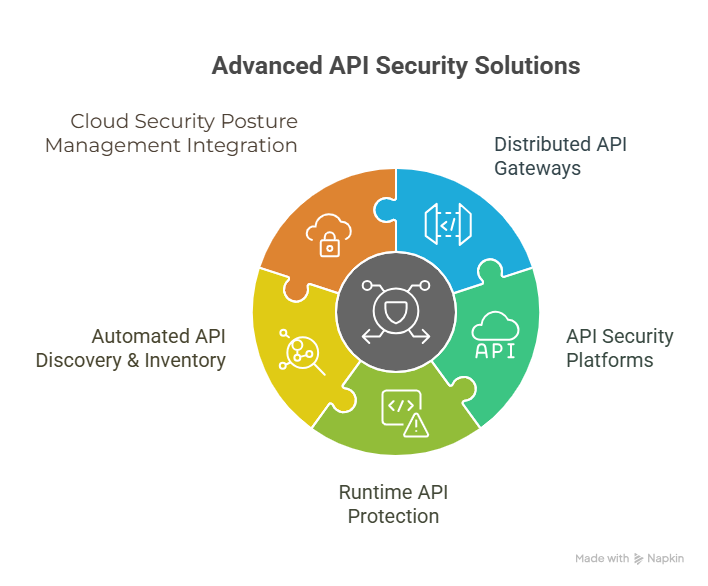
- Distributed API Gateways with Enhanced Security: More intelligent gateways capable of enforcing granular access control, rate limiting, and sophisticated threat protection at the network edge.
- API Security Platforms (ASP): Comprehensive platforms offering API discovery, posture management, advanced threat detection, and streamlined incident response, specifically designed for APIs.
- Runtime API Protection: Tools that continuously monitor API behavior during execution, detect anomalies, and immediately block attacks, often utilizing AI/ML capabilities.
- Automated API Discovery & Inventory: Continuously identifying all active and ‘shadow’ APIs across distributed environments, providing essential visibility into the entire attack surface.
- Seamless Integration with Cloud Security Posture Management (CSPM): Harmonious integration with broader cloud security tools to ensure consistent policies and unified visibility across the entire cloud footprint.
Is Your Organization Prepared for the API Security Challenge?
The API security battleground in 2025 is both dynamic and demanding.
Organizations that adopt a comprehensive strategy—one that marries advanced technology, empowers developers, adheres to stringent standards, and fosters continuous vigilance—will be optimally positioned to safeguard their digital assets and preserve stakeholder trust.
Overlooking these evolving trends is no longer a viable option; it directly leads to substantial business risk.
Enquiry Now, how to protect your network or web application




