A Web Application Firewall (WAF) is a specialized security solution designed to protect web applications by filtering, monitoring, and blocking malicious HTTP/S traffic between the internet and the web application server.
Unlike traditional firewalls that focus on network-level traffic, a WAF operates at the application layer (Layer 7 of the OSI model), inspecting the content of web requests to identify and prevent attacks targeting web applications
Why is a WAF Important for Online Business
Web applications are common targets for cyberattacks due to their accessibility over the internet and the sensitive data they often handle. Attacks such as SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), file inclusion, and cookie poisoning are frequent causes of data breaches.
A WAF acts as a critical shield, blocking these attacks before they reach the application, thereby safeguarding valuable data and maintaining application integrity
How does a Web Application Firewall (WAF) Work?
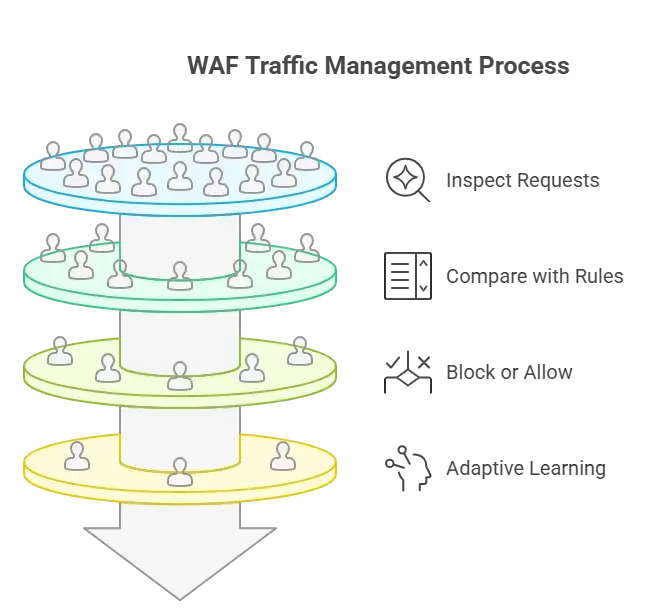
A WAF functions as a reverse proxy, sitting between the client (user) and the web application server. All incoming requests and outgoing responses pass through the WAF, which inspects them against a set of security policies or rules to identify malicious activity.
If a request violates these rules, the WAF can block, log, or allow it based on the configured mode.
- Reverse Proxy Role: The WAF intercepts client requests and forwards only safe requests to the backend server, protecting the server from direct exposure.
- Policy-Based Filtering: WAFs use policies that define what constitutes safe and unsafe traffic. These policies can be based on:
- Negative Security Model (Blocklist): Blocks known malicious patterns.
- Positive Security Model (Allowlist): Allows only pre-approved traffic patterns.
- Hybrid Model: Combines both approaches for balanced security.
- Advanced Inspection: Modern WAFs leverage machine learning and threat intelligence to detect zero-day attacks and sophisticated threats automatically.
Common Attacks Mitigated by WAFs
WAFs protect against many of the OWASP Top 10 vulnerabilities and other common web attacks, including:
- SQL Injection: Attackers inject malicious SQL queries to manipulate databases.
- Cross-Site Scripting (XSS): Malicious scripts are injected into web pages viewed by other users.
- Cross-Site Request Forgery (CSRF): Unauthorized commands are transmitted from a user that the web app trusts.
- File Inclusion Attacks: Unauthorized files are included and executed on the server.
- DDoS Attacks: WAFs can implement rate limiting and blocking to mitigate Distributed Denial of Service attacks.
Web Application firewall(WAF) Deployment Models
WAFs can be deployed in various ways depending on the organization’s infrastructure, security needs, and management preferences:
- Cloud-Based WAF: Hosted and managed by third-party providers, offering scalability and ease of use without on-premises hardware. Ideal for cloud-hosted applications.
- On-Premises Appliance: Physical devices installed within the network, providing dedicated protection for organizations with strict compliance or control requirements.
- Software-Based WAF: Installed on existing infrastructure or servers, offering flexibility and customization. WAF as a Service (WAFaaS): A fully managed cloud service where the provider handles updates, tuning, and maintenance, allowing organizations to outsource WAF management.
Modes of Operation
- Log Mode: The WAF monitors and logs suspicious traffic without blocking it, useful for testing and tuning rules.
- Block Mode: Actively blocks malicious traffic based on security policies, suitable for live production environments.
Key features and Capabilities of WAF
- IP Fencing and Geo-Blocking: Blocking traffic from suspicious IP addresses or specific geographic regions.
- Request Inspection: Deep analysis of HTTP headers, body, cookies, and query parameters to detect anomalies.
- Rate Limiting: Controls traffic volume to mitigate DDoS attacks.
- Machine Learning: Automated policy updates and threat detection to keep pace with evolving threats.
- Reverse Proxy Caching: Improves performance by caching responses and reducing load on backend servers.
WAF vs Other Security Solutions
| Feature | WAF | IPS (Intrusion Prevention System) | NGFW (Next-Generation Firewall) |
|---|---|---|---|
| Focus | Application layer (HTTP/S traffic) | Network and session layers (various protocols) | User and network traffic, with advanced filtering |
| Protection Scope | Web app attacks (XSS, SQLi, CSRF) | Broad network attacks | User-based policies, URL filtering, malware protection |
| Deployment | Reverse proxy | Inline or passive network device | Forward proxy or network gateway |
| Customization | Application-specific policies | Signature and policy-based | User and application-aware policies |
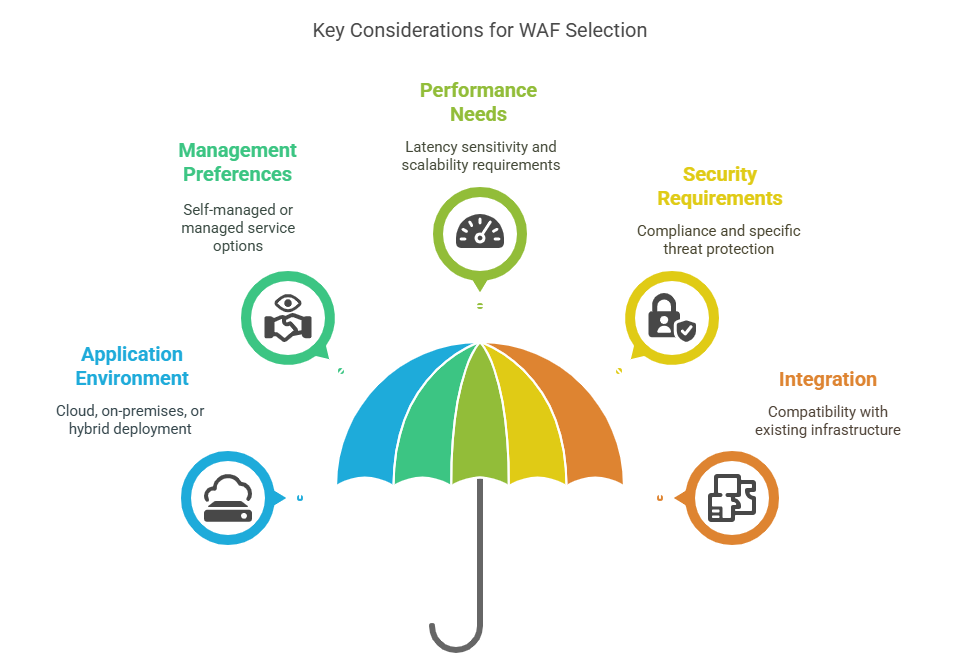
What to consider while choosing right WAF
When selecting a WAF, consider:
- Application Environment: Cloud, on-premises, hybrid.
- Management Preferences: Self-managed vs. managed service.
- Performance Needs: Latency sensitivity, scalability.
- Security Requirements: Compliance, specific threat protection.
- Integration: Compatibility with existing infrastructure and security tools.
Emerging Trends in WAF Technology
Modern WAFs increasingly incorporate AI and machine learning to automate threat detection and policy updates, reducing manual intervention and improving response times to new vulnerabilities.
Integration with broader Application Security platforms (WAAP) enhances protection by combining WAF with API security, bot management, and DDoS mitigation
Check Haltdos WAF: Flexible Pricing for Every Need
Haltdos offers a flexible, tiered pricing model for its Web Application Firewall, making enterprise-grade security accessible to organizations of all sizes:
Free Tier (Community Edition): The Haltdos Community Edition (CE) is a fully free, self-managed WAF that protects against OWASP Top 10 threats, DDoS attacks, and bot traffic. Ideal for startups and small businesses, it includes SSL management, geo-fencing, and real-time attack analytics.
Learn , How to install Free Community WAF step-by-step?
Paid Tier (Professional Edition): The Haltdos Professional Edition (PE) operates on a usage-based model, starting with a free allowance of 100,000 requests. Beyond this, pricing scales at $30 USD per million requests, offering advanced features like API security, bot mitigation, and compliance with standards like GDPR, HIPAA, and PCI-DSS.
Customized Solutions: For enterprises with high traffic volumes or specialized needs, Haltdos provides tailored pricing based on deployment type (shared/dedicated), advanced threat intelligence requirements, and compliance mandates.
A Web Application Firewall (WAF) is an essential security layer that protects web applications from a wide range of cyber threats by filtering and monitoring HTTP/S traffic. By deploying a WAF, organizations can defend against critical vulnerabilities, reduce the risk of data breaches, and ensure the availability and reliability of their web services. Whether deployed on-premises, in the cloud, or as a managed service, a WAF remains a cornerstone of modern web application security.
For organizations looking to enhance their security posture, exploring solutions like those offered by Haltdos can provide advanced application security capabilities integrated with WAF functionality, delivering comprehensive protection against evolving threats.




