In the ever evolving landscape of cybersecurity, the battle against malicious actions continues to intensify. Amongst the most concerning threats, are bot attacks and Distributed Denial of Service (DDoS) attacks, both of which can disrupt online services, and compromise data integrity.
In this blog post, we’ll talk about how Haltdos leverages cryptographic techniques such as Proof-of-Work (PoW) systems in effectively in combating bot attacks and Layer 7 DDoS attacks.
Introduction to Proof of Work Systems
An interesting concept in cryptography is the concept of PoW. The idea behind PoW is to make a participant solve a complex mathematical puzzle. If the participant provides a valid answer, he/she demonstrates to the challenger the effort put into solving the puzzle – hence, his / her Proof of Work.
For a PoW system to work, the algorithm should ensure that the puzzle is hard to solve i.e., it requires use of computational power, but quick and simple to verify. In other words, both the participant and the challenger must come to a consensus on the solution to the puzzle – with the challenger taking much less effort to verify the answer presented by the participant.
Origins of Proof of Work Systems
The origin of PoW can be traced back to 1993 when Cynthia Dwork and Moni Naor were looking for a solution to deter email spam and DoS attacks. Their paper on pricing via processing outlined the basics of proof-of-work.
In 1997, Adam Black integrated their idea into an algorithm. His algorithm made it difficult for spammers to send large volumes of emails by requiring senders to include a computationally expensive string of characters in the email. The solution to spam was essentially increasing the cost to send individual emails. This experiment proved that you could use computational difficulty to represent the value of something online. This inspired others to see if they could use the same idea to make a digital representation of cash.
The idea made an appearance again in Nick Szabo’s so-called ‘Theory of Collectibles’ and the paper “Shelling Out: The Origins of Money.” In 2004, these ideas inspired Hal Finney to create a version of it called reusable proof-of-work. And in 2009, Satoshi Nakamoto famously created the proof-of-work consensus mechanism for Bitcoin. It was the first decentralized implementation that solved the double spending problem and made bitcoin the first successful form of digital cash.
How Proof of Work System works
The following explains how a PoW system works to deter email spams:
- Selection of Parameters: A system sets specific parameters, including the target difficulty level, and the algorithm to be used for hashing.
- Computational Work: To send an email or perform an action, the sender’s computer must perform a certain amount of computational work. This usually involves repeatedly hashing the data (such as the content of the email) with slight variations until a hash value is generated that meets the specified difficulty level.
- Proof Generation: Once the sender’s computer finds a suitable hash value, it includes this value as a “proof” in the email header or action request.
- Verification: The recipient or recipient’s system can quickly verify that the sender has done the required computational work by checking the hash value against the target difficulty level. If the proof is valid, the email is accepted; otherwise, it’s rejected.
To stop spam and attacks, the algorithm effectively converts computational labour into a type of payment. It makes sure that sending emails, or doing actions, needs a substantial amount of work, which might take a lot of time and resources for spammers or attackers. Legitimate users can also get around this effort, but often at a far lower cost because of their unique need or interest.
In essence, the algorithm technique converts computational effort into evidence that the sender put up a particular amount of effort to create the email. It takes more processing to find a valid hash as complexity increases, making it more challenging for spammers to send a lot of emails.
Because it takes a substantial amount of computing work to change prior transactions, PoW is reliable and secure. Alternative consensus procedures, like as Proof of Stake (PoS) and Proof of Authority (PoA), have been created in response to these worries to overcome some of the problems of PoW.
Move to Proof of Stake (PoS) Systems
While PoW has been successful in securing blockchain networks, it has also been criticized for its high energy consumption and potential environmental impact due to the substantial computational power required to solve the puzzles. As a result, alternative consensus mechanisms like Proof of Stake have been developed to address these concerns.
Like PoW, PoS is another consensus algorithm. PoS relies on validators who are chosen to create new blocks and validate transactions based on the amount of cryptocurrency they “stake”, or lock up as collateral.
Ethereum, Bitcoin’s top competitor, used PoW on its blockchain until September 2022, when they transitioned to using a PoS system instead.
How WAFs protect against Bots and DDoS attacks?
WAF solutions have multiple techniques to defend against Bots and DDoS attacks. Some of them include Rate Limiting, Challenge-Response, Geo Fencing (IP, Country, ASN), Behaviour Analysis, etc.
For brevity, I will focus on Challenge-Response and discuss other mitigation techniques in another blog post. In Challenge-Response technique, WAF solutions send a challenge and expect a valid response before allowing the user to access the application under protection. There are multiple Challenge-Response mechanisms used in WAF:
- SYN Challenge: This is a network challenge when the user is trying to establish a connection with the application. The WAF solution creates a cryptographic SYN Cookie during a 3-way TCP connection handshake to prevent attackers from exhausting WAF resources through IP spoofing.
- Captcha Challenge: WAF sends an HTTP challenge requiring users to solve CAPTCHAs before accessing certain parts of your application. This mechanism can help distinguish between human users and bots. CAPTCHAs are designed to be difficult for automated bots to solve.
- JavaScript Challenge: Similar to Captcha, this challenge involves dynamically generating puzzles, or other interactive elements that require the user to execute JavaScript code to successfully complete the challenge.
With advanced Bots leveraging Artificial Intelligence, JavaScript or Captcha challenge are no longer hard to beat.
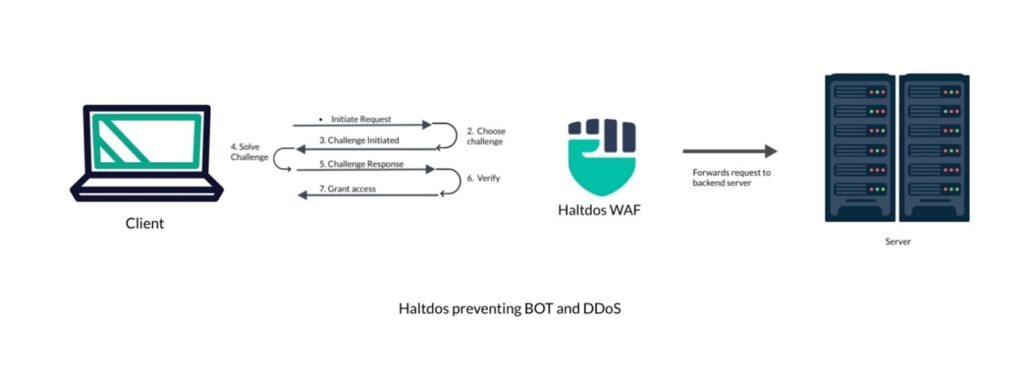
Introducing Proof of Work Challenge
Similar to JavaScript Challenge, this Challenge-Response mechanism imposes a computational cost on the user wanting to access certain part of the application. The challenge demands that the client complete a specified amount of proof-of-work before processing a request from a client to access a resource (such as a webpage). The client’s request is handled only if their proof of work is legitimate; if not, it is rejected. Each request now has a processing cost, making it more difficult for attackers to send multiple requests.
Haltdos WAF allows users to configure the degree of complexity of Proof-of-Work Challenge. Higher the degree, more expensive for attackers to complete the challenge. In Haltdos, this degree ranges from 1-10. While a PoW challenge of degree 1 induces < 0.5% CPU consumption, a PoW challenge of degree 5 may induce CPU consumption as high as 60% – thus greatly slowing down the request rate from malicious bots.
Combining with Behaviour Analysis
Haltdos WAF has a robust behavioural engine to detect malicious activities. Haltdos WAF allows Proof of Work challenge to integrate with behaviour analysis to dynamically change PoW Challenge degree for repeat offences – making it progressively harder for attackers to perpetrate their attack.
Conclusion
The crypto challenge presents a dynamic battleground where cryptographic techniques intersect with the world of bot traffic mitigation. As bots become more sophisticated, the application of cryptography becomes increasingly vital to maintaining the integrity of digital interactions. Proof of Work can make such attacks slower, more challenging and expensive by necessitating a large amount of computing labour on the part of the attacker. While they may not be a comprehensive solution on their own, they can certainly contribute to blocking bots and mitigating DDoS attacks.
By leveraging innovative cryptographic solutions such as puzzles, zero-knowledge proofs, blockchain technology, and biometric authentication, businesses and website owners can fortify their defences and ensure a safer online environment for all. The crypto challenge is an ongoing saga that calls for constant vigilance and collaboration within the tech community to stay one step ahead of the ever-evolving bot threat.




